Introduction
In today’s digital landscape, software development services enable businesses to thrive in the competitive market. However, with the increasing importance of data security and privacy, software development companies must establish robust information security management systems. ISO/IEC 27001, an internationally recognized standard, comes into play. This article will explore how implementing ISO/IEC 27001 can enhance software development services and protect sensitive information.

What is ISO/IEC 27001?
ISO/IEC 27001 is an internationally acknowledged norm that offers a structure for the creation, execution, upkeep, and ongoing enhancement of an Information Security Management System (ISMS) within an organization. The main goal of ISO/IEC 27001 is to guarantee the confidentiality, integrity, and accessibility of information, safeguarding it against unauthorized access, disclosure, manipulation, and loss.
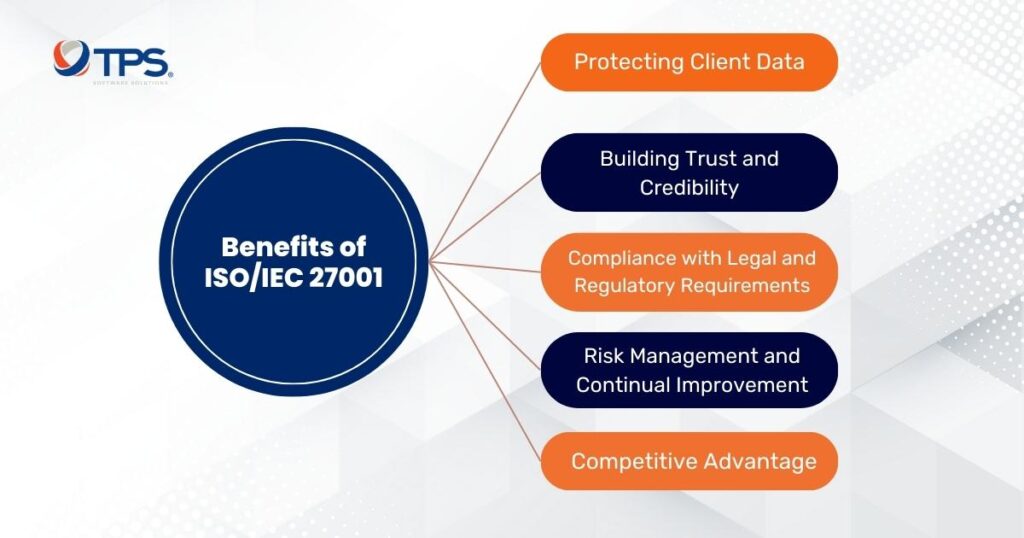
The Benefits of ISO/IEC 27001
Acquiring ISO/IEC 27001 can significantly benefit your software development service.
Protecting Client Data
One of the key benefits of implementing ISO/IEC 27001 in software development services is the enhanced protection of client data. By adhering to the standard’s requirements, software development companies can establish and maintain strict control over information security. The work includes implementing robust access controls, encryption techniques, secure coding practices, and secure data storage measures. Clients have trust that their sensitive information is safe against potential security breaches.
Building Trust and Credibility
Trust is crucial for businesses. By obtaining ISO/IEC 27001 certification, software development companies can showcase their commitment to information security and build trust with their clients. The certificate is a testament to the company’s adherence to best practices and compliance with international standards. It assures clients that your company handles the project with the utmost care and security.
Compliance with Legal and Regulatory Requirements
Software development companies often deal with sensitive data. They are subject to various legal and regulatory requirements, such as the European General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA) in the United States. ISO/IEC 27001 provides a comprehensive framework that helps organizations align their processes and practices with these requirements. Compliance with such regulations becomes more manageable when the company already has an established ISMS.
Risk Management and Continual Improvement
ISO/IEC 27001 emphasizes a risk-based approach to information security management. Software development companies can identify and mitigate potential security threats and vulnerabilities by conducting regular risk assessments and implementing appropriate controls. This proactive approach minimizes the likelihood of security incidents and helps protect against data breaches. Moreover, ISO/IEC 27001 encourages continual improvement through periodic audits, reviews, and corrective actions, ensuring that security measures remain practical and current.
Competitive Advantage
ISO/IEC 27001 certification can provide a significant competitive advantage in software development. Many clients prioritize working with companies that prioritize information security. By demonstrating compliance with ISO/IEC 27001, software development companies can differentiate themselves from competitors and position themselves as trustworthy partners for clients prioritizing their sensitive data’s security.
How Software Development Services Obtain ISO/IEC 27001?
Obtaining ISO/IEC 27001 certification for a software development service involves several key steps. Here’s a general overview of the process:
Determine Readiness
Assess your organization’s current information security management practices against ISO/IEC 27001 requirements. Identify any gaps and areas that need improvement.
Define Scope
Clearly define the scope of your Information Security Management System (ISMS) implementation. The range includes specifying the boundaries of the systems, processes, departments, and locations covered by the certification.
Develop Policies and Procedures
Create information security policies and procedures that align with the ISO/IEC 27001 standard. These documents should outline how your organization will address information security risks, protect sensitive data, and ensure compliance with applicable laws and regulations.
Perform Risk Assessment
Conduct a comprehensive risk assessment to identify and analyze potential security risks and vulnerabilities specific to your software development service. This assessment will help you determine the security controls and safeguards to mitigate identified risks.
Implement Controls
Implement the necessary security controls and measures identified during the risk assessment phase. These may include access control mechanisms, secure coding practices, encryption techniques, vulnerability management processes, incident response procedures, etc. Ensure that these controls align with the ISO/IEC 27001 requirements.
Documentation
Document all relevant information, including policies, procedures, processes, and controls implemented in your ISMS. This documentation will serve as evidence during the certification audit.
Internal Audits
Conduct internal audits to assess the effectiveness and compliance of your ISMS. These audits help identify gaps or areas needing improvement before the formal certification audit. Pick an accredited certification body to conduct the certification audit. Ensure the certification body has the necessary expertise in ISO/IEC 27001 assessments.
Certification Audit
The certification audit consists of a two-stage process. Stage 1 involves a review of your ISMS documentation and readiness for the certification audit. Stage 2 is the primary certification audit, where the certification body assesses the implementation and effectiveness of your ISMS.
Corrective Actions
Address any non-conformities or findings identified during the certification audit. Take corrective actions to rectify the identified issues and ensure compliance with the ISO/IEC 27001 standard.
Certification Decision
Following the certification audit and the completion of any corrective actions, the certification body will decide on your ISO/IEC 27001 certification. If you satisfy all the requirements, you will earn the certificate.
Ongoing Compliance
Maintain and continuously improve your ISMS to ensure ongoing ISO/IEC 27001 compliance. It includes regular internal audits, management reviews, and addressing changes in information security risks or business processes.
Conclusion
ISO/IEC 27001 is invaluable for software development companies looking to strengthen their information security management practices. By implementing the standard’s requirements, companies can protect client data, build trust, comply with legal and regulatory requirements, manage risks effectively, and gain a competitive edge. As the demand for secure software development services continues to grow, ISO/IEC 27001 certification becomes a key differentiator for organizations striving to provide their clients with the highest level of information security.